The Cyber Threat Intelligence (CTI) service from Logicalis is the foundation for a resilient security model, providing systematic threat context collection and supporting the development of your long-term cybersecurity roadmap.
360 Protection with Real-Time Intelligence
Our approach covers the critical pillars of modern security.
Service Portfolio
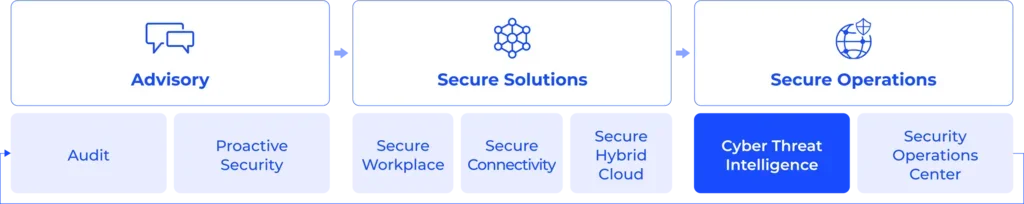
Cyber Threat Intelligence Offer
Brand & Domain Impersonation
• Monitoring malicious advertising and DNS (fraud and pre- phishing)
• Identification of brand abuse, even without malicious domains
• Unlimited takedown with evidence collection

SEO Poisoning
• Verification of brand entries in search engines and social media
• Detection of fraudulent advertising and abusive use of brand
• Takedown included for confirmed incidents

Leaked Credentials
• Identification of leaks in the public, deep, and dark web
• Automatic testing via API with risk assessment

Critical Accounts Exploitation
• Monitoring of high-value human assets
• Integration with Leaked Credentials to detect non-corporate access

Supply Chain Control (SCC)
• Monitoring of partners with infrastructure access
• Detection of supply chain threats on the dark web
• Focus on third parties with potential impact on client security
Perimeter Monitoring
• Continuous monitoring of online assets
• Identification of vulnerabilities and misconfigurations

Suspicious Authentication Alert
• Monitoring of O365/email and VPN accesses
• Risk scoring based on reputation and leaked credentials
• Alerts with incident severity assessment

Service Features
• OSINT Assessment (every 6 months)
• Real-time Dashboard
• Domain and Ad Takedown
• Service Reports
• Comprehensive Blocking of Compromised Accounts